Nano Price
(XNO/USD)

Guarda Wallet offers a secure and user-friendly platform for managing cryptocurrencies, tokens in a non-custodial manner.

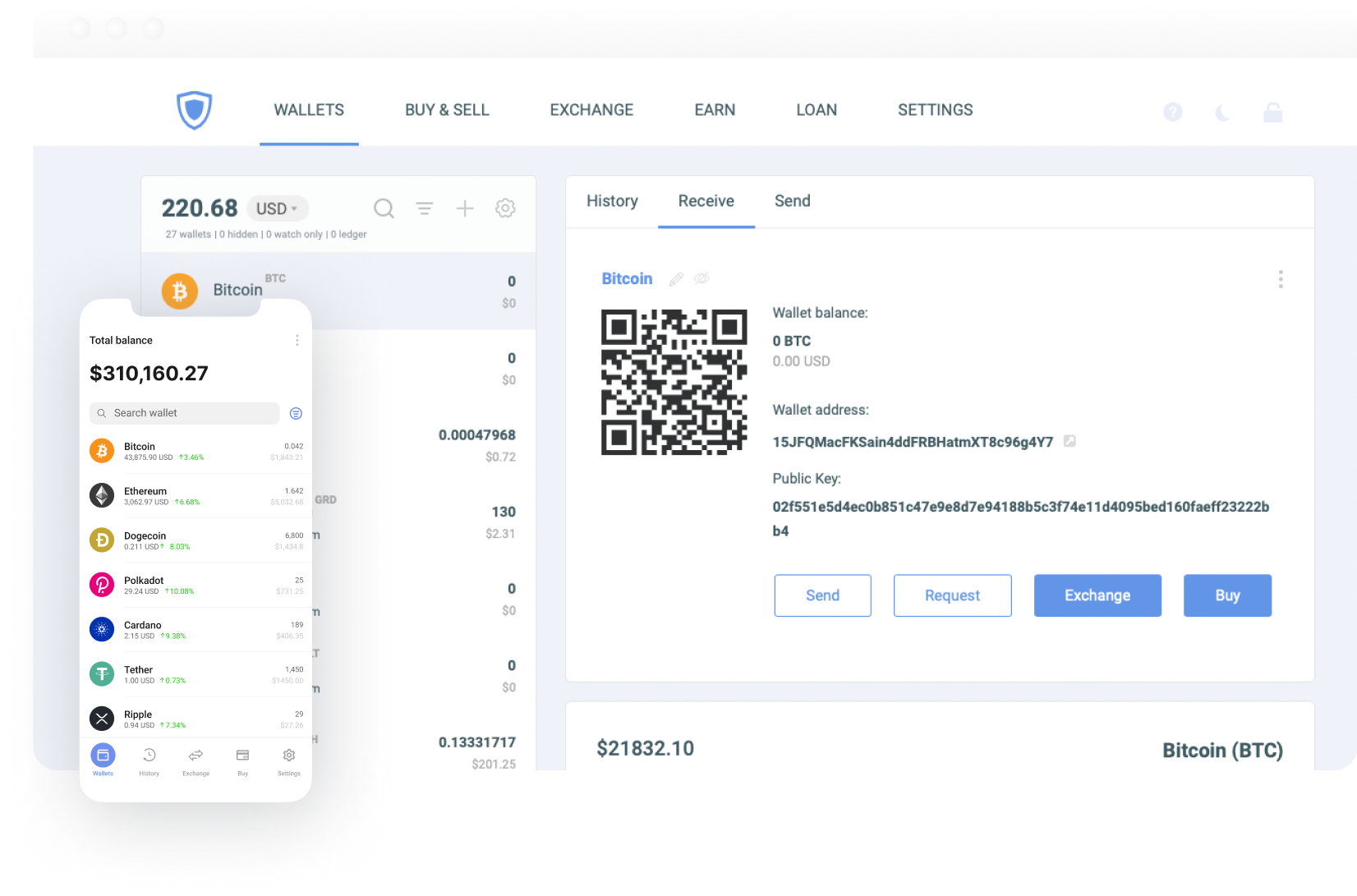
Create Nano wallet to transform your crypto experience with Guarda multi-currency wallet. Buy, send, receive, and store your Nano quickly and securely.
Guarda is a powerful and user-friendly multi-currency wallet that allows you to securely store and manage your crypto. With Guarda, you can easily create online Nano wallet app for PC, Mac, iOS and Android
Create WalletOur cutting-edge wallet platform lets you stake your crypto and earn money simply by supporting the network. With our user-friendly interface and industry-leading security, Guarda is the perfect choice for anyone looking to earn passive income on their crypto investments.
Stake Now
Current Holdings Value
Annual Yield

You hold your own keys and have full control over your funds

Your crypto and personal information are safe

Access your wallets from any device, anywhere

Over 50 cryptocurrencies can be stored and exchanged

Transaction fees adjust based on network congestion

Representatives are available at all times
Guarda is one of the best wallets according to Investopedia.com and Hackernoon.com for Nano. Guarda is a non-custodial wallet that supports more than 400K+ assets. Use an online wallet right in your browser or download a mobile version.
You can download the application from the Apple AppStore, or Google Play, or install a desktop wallet. You can also use an online wallet. Create an account on Guarda; Set a strong password and save your wallet backup; Create a wallet and add your XNO.
Download Guarda from AppStore or Google Play; Create an account on your Guarda Wallet; Tap the “Receive” button in app; Paste the generated address or scan the QR code when sending coins from an external wallet or exchange to Guarda.
Guarda is a non-custodial crypto wallet. Guarda stores no
private data, backup files, or keys, and no one has access
to the user's wallet. Users are the only ones who have
access to private information.
Security features
include: fingerprint authorization; PIN code; backup file